How disruption can help lead to innovation in today’s security programs
Our idea of modern workspace has been disrupted, redefining security’s role in the workplace. The continuing unknowns on when and how to reopen have made one thing clear—the distributed workforce model is here to stay. Physical security departments will have to not only continue to protect the workspace but maintain health and safety procedures and manage employee awareness. The “New Normal” also means rethinking some critical physical security questions:
How do you manage your security portfolio in this distributed environment?
What best practices can be effective in making the right decisions in an evolving dynamic?
How do you leverage resources and tools to achieve success in short and mid-term objectives?
Examining each of these three pillars as they apply to your team’s priorities will help to establish a clear roadmap for moving forward.
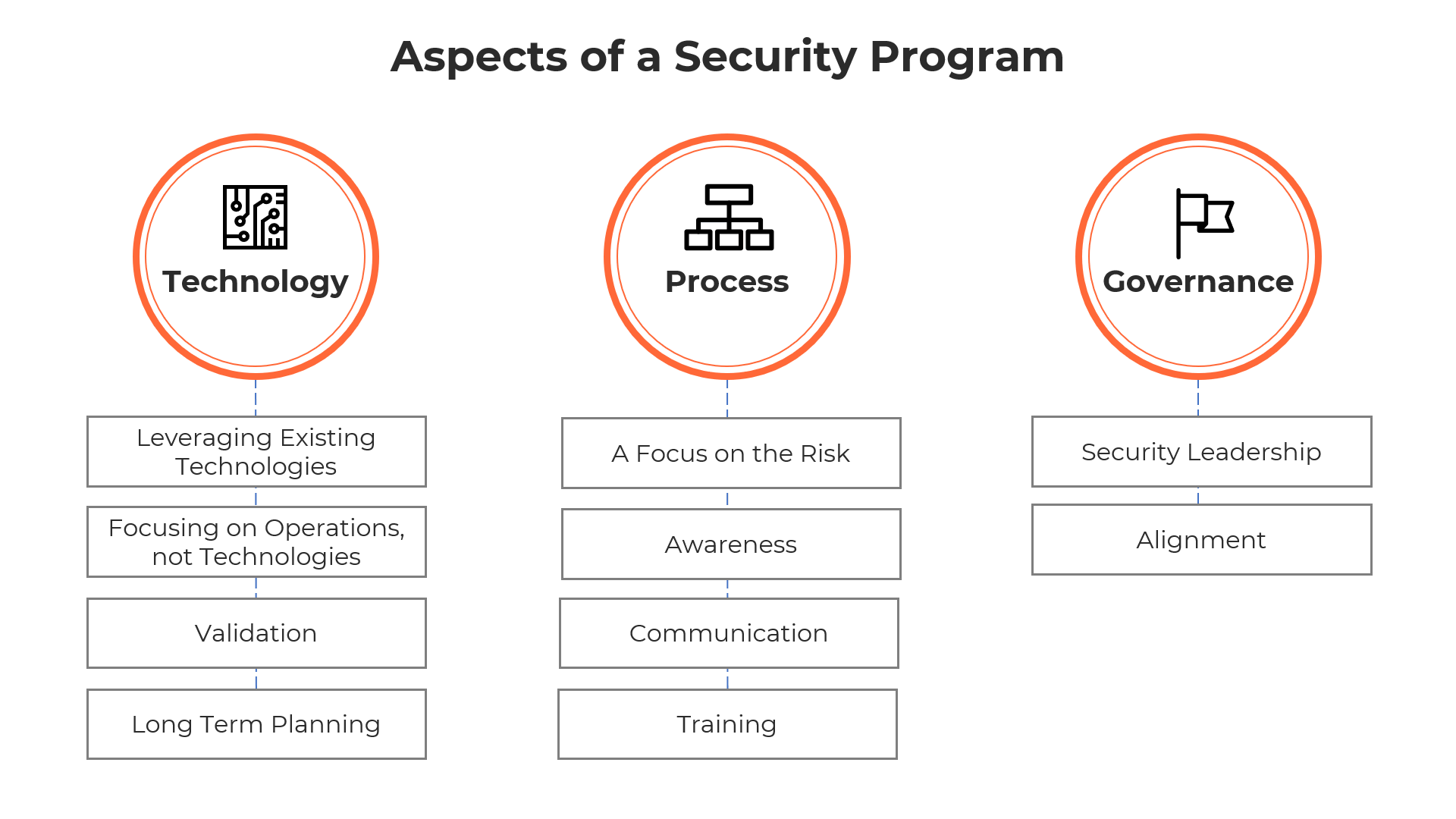
Technology
How do you monitor alarms and manage the physical security coverage?
What technology decisions do you make to maintain an effective security program?
How do you effectively leverage supply chain and external vendors?
We have seen a major increase of technology catered toward workplace health and safety. These technologies now include contact tracing, health screenings, sanitization, and dynamic scheduling of access. Security departments, who traditionally focused solely on security and safety, have suddenly become responsible for buying, implementing and managing the new technologies often with quick turnaround mandates.
As the workforce model continues to evolve and new technologies become available, security departments will need to consistently evaluate and decide on which solutions will best meet their needs.
When making a decision on new technology, consider the following:
Leveraging Existing Technologies: Most security management systems have functionality that may meet your requirements without having to purchase additional modules or licenses. An example may be utilizing advanced reporting from the access control system. The use of analytical tools, such as PowerBI can help visualize employee space usage in a dashboard. A simple export and integration may be sufficient and much more cost effective than purchasing a new contact tracing module.
Focusing on Operations, not Technologies: Conduct and assessment of your current risk profile and validate operational needs with a review of policies, procedures, and stakeholder agreements. Review existing vendor contracts and service level agreements (SLAs) to close gaps. An operations review can yield significant value to the business and reduce the need to invest in more expensive efforts.
Validation: Evaluate what’s available within the organization against market solutions by working with Procurement to issue technical Requests for Information (RFI) and vendor demonstrations to compare how the technology will help achieve your goals. Conduct Proof of Concepts (POC) for shortlisting solutions to ensure not only they work as suggested, but that they work in your environment against your physical, infrastructure and operational conditions.
Long Term Planning: Incorporating post-pandemic functionality into technology decisions can create a more effective lifecycle return on your investment. Insights identified during the RFI phase will provide content to support a business case to deliver an automated and manageable program.
Process
How do you best manage incidents and investigations in the new environment?
What projects or priorities can be accomplished in tighter budget cycles?
How do you manage new roles and responsibilities around health and safety protocols?
With regards to process, it would be a mistake to think that what worked well before the pandemic will continue to work well in the future. As a direct result of the current health crisis, certain aspects of security have taken on a new and vital significance.
A Focus on the Risk: All security needs are borne out of a risk to the organization, its people, or infrastructure. These risks may be safety, operational, reputational, or financial. Focusing on continual and consistent risk assessment and how to mitigate identified risks often leads to the correct business case. This approach also allows organizations to examine all possible solutions and develop a mitigation strategy that combines people, process, and technology.
Awareness: The security program’s purpose and its requirements should be clear to management and employees. A strong sense of awareness allows the management to stand behind the program and ensures employee participation. Awareness campaigns should also always include feedback opportunities for employees so that they are engaged, and their concerns are heard.
Communication: Communication and collaboration among different levels of the organization is vital to the security program’s success. It raises the level of awareness, allowing all parties to understand each other and work towards common goals. Framing communication around overall risk can help reducing any institutional or territorial barriers.
Training: With security departments taking on additional responsibility around health and safety, training of staff to properly screen, advise and educate employees is critical. Training is also crucial to ensure proper communication and escalation processes are followed correctly to mitigate impacts from incidents.
Governance
How do you raise proper levels of awareness and communication on best security practices?
How do you properly collaborate with your leadership and other parts of the organization?
How can you develop an effective business case for your security program?
A successful selection of technologies and maintenance of programs is difficult without the proper governance structure in place. The governance structure connects all layers of the organization and clearly defines the role of security employees, their appropriate tasks, and how they interact with the broader organization:
Security Leadership: A vital component of governance is placing security at the same table as other leadership within the organization. Security is often perceived as a back of house operation managed by another department, such as HR or Facilities. While that reporting structure is adequate, security leadership should be an advocate in the C-Suite, who can articulate physical security risks, represent the security program’s business case and help align it to corporate strategy.
Alignment: A well thought out governance model allows security and corporate leadership to be aligned with the company’s direction. Alignment is crucial to ensure the security program enables the organization to thrive and security’s funding is spent effectively, with a focus on risk. Alignment also allows the company’s leadership to understand the purpose and investment of its security program and can therefore, champion security and safety as part of the overall culture of the firm.
Physical security departments’ scope of responsibilities has increased dramatically in the last year. Stay tuned as we break down new technologies and strategies to ensure the health and safety of your company and employees.
About Atriade
Atriade Atriade has worked on over 500+ projects, in 60+ industries, in 30+ countries. If you are ready to get expert assistance in creating your governance plan that will set you apart from your competitors, we are here to help. Our management team carries a lifetime of experience in all areas of Physical Security and Electronic Security that we are ready to put to work for your unique business and team.
Visit us online at Atriade.com
Connect with us on LinkedIn
Subscribe to our LinkedIn Newsletter: Take A Risk